Phishing is still one of the biggest threats facing UK businesses. It is simple, cheap for criminals to run, and incredibly effective. Most cyber attacks start with someone clicking a link or opening an attachment that looks safe at first glance. Once that happens, the damage can be fast and costly.
If you run a business, you do not need to become a cybersecurity expert. You just need to understand what phishing looks like today and put the right protection in place. This guide explains what phishing is, how to spot it, the latest trends in 2025, and what you can do to keep your staff and data safe.
Phishing is when criminals pretend to be someone you trust so they can trick you into giving away information, money, or access to your systems. They usually impersonate banks, delivery companies, government departments, suppliers, or even your own staff.
Most phishing attacks arrive as:
• Emails
• Texts (smishing)
• Phone calls (vishing)
• Fake login pages
• Social media messages
Criminals are getting better at making these messages look convincing. That is why phishing remains one of the easiest ways for attackers to breach a company’s security.
Phishing is no longer just about stealing passwords. It can lead to:
Ransomware attacks
Criminals gain access to your systems and lock your data until you pay.
Business email compromise
Attackers take over your email account and send fraudulent messages to staff or customers.
Financial loss
Fake invoices, payment redirects, or fraudulent transactions can cost companies thousands.
Personal and confidential information can be exposed, leading to fines and reputational damage.
Operational downtime
If your systems are compromised, your business may grind to a halt.
For many small and mid sized businesses, a successful attack can be devastating. The good news is that there are clear warning signs and practical steps that make a huge difference.
Even the most professional looking messages usually have something that feels a little off. Here are the signs staff should look for:
Anything that says “act now”, “payment overdue” or “your account is closing today” should be treated with suspicion.
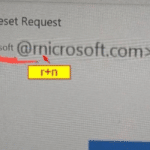
Hover over the sender’s email address. Criminals often use addresses that look close to legitimate ones.
Attackers are improving, but mistakes still slip through.
Hover over the link and check the real URL. If it looks strange or unrelated, do not click it.
Invoices, PDFs, and ZIP files are common tricks used to deliver malware.
If a colleague suddenly emails you asking for bank details or gift cards, double check before responding.
Training staff to pause, check, and question saves businesses every day.
Criminals constantly evolve their tactics. Here are the trends that are becoming more common this year.
Attackers now use AI tools to create messages that look professional, personalised, and far more convincing than older phishing attempts.
Some fraudsters use AI to mimic a colleague’s voice. Businesses should not rely on voice alone for authorising payments.
Attackers reproduce login screens and ask you to “sign in again”, stealing your credentials.
Criminals study relationships between companies and then impersonate a real supplier to redirect payments.
You scan a QR code that looks legitimate and end up on a fraudulent site.
Being aware of these trends helps you keep your guard up.
Do not panic. Act quickly and follow these steps:
Disconnect from the internet
This limits what malware can do.
Report it immediately
Tell your IT team or managed support provider. Speed matters.
Start with your email and any accounts linked to the suspicious message.
Scan your device
Run a full antivirus and anti-malware scan.
Review recent activity
Look for unauthorised logins, password resets, or unusual emails sent from your account.
The worst thing you can do is ignore it. Quick action often prevents major damage.
This is where prevention makes a real difference. The following measures can dramatically lower your risk.
People are your first line of defence. Simple awareness training, short refreshers, and realistic phishing tests help staff spot scams before they spread.
Even if an attacker steals a password, they cannot log in without the second step of verification.
Modern filtering solutions block dangerous links, attachments, and known malicious senders before they reach your staff.
Staff should avoid reusing passwords or using simple ones that can be guessed.
Out-of-date software is much easier to exploit.
A proactive IT partner will detect suspicious activity, patch vulnerabilities, and respond quickly if something goes wrong.
If a phishing attack leads to ransomware, a reliable cloud backup can save the day.
The most resilient businesses take a layered approach. No single tool or policy is perfect, but together they create strong protection.
At Silver Lining, we work with companies across the UK to reduce their exposure to cyber threats, including phishing. Our approach focuses on prevention, quick response, and long term security.
Proactive IT monitoring
We keep an eye on your systems 24 hours a day so suspicious activity is spotted early.
Email security and filtering
Dangerous content is blocked long before it reaches your inbox.
We help businesses meet the requirements and strengthen their overall security.
Secure cloud backup and recovery
If a breach does happen, your data is protected.
We help teams understand the risks and stay alert to new threats.
Dedicated Account Manager
You always have someone who knows your setup and can help you plan your next steps.
Cybersecurity can feel overwhelming, but with the right partner it becomes manageable and far less stressful.
Phishing is not going away, and criminals are getting more advanced. But with the right training, tools, and support, businesses can stay ahead of these attacks. Awareness is half the battle. The rest is making sure your systems and staff are properly protected.
If you would like help improving your cybersecurity or want a review of your current setup, Silver Lining can guide you. Just let me know if you want a contact page link or a short call to action added at the end.